Free Link Scanner & Phishing Forensics Tool
ZeroTrust Link Scanner
Advanced URL Threat Intelligence & Security Analysis
System Documentation v3.3
Most scanners are just browser extensions. We use a Server-Side Engine (scan_engine.php) to ping the target website from our secure cloud. This allows us to inspect SSL Certificates, HTTP Headers, and DNS records that your browser cannot access directly due to security restrictions.
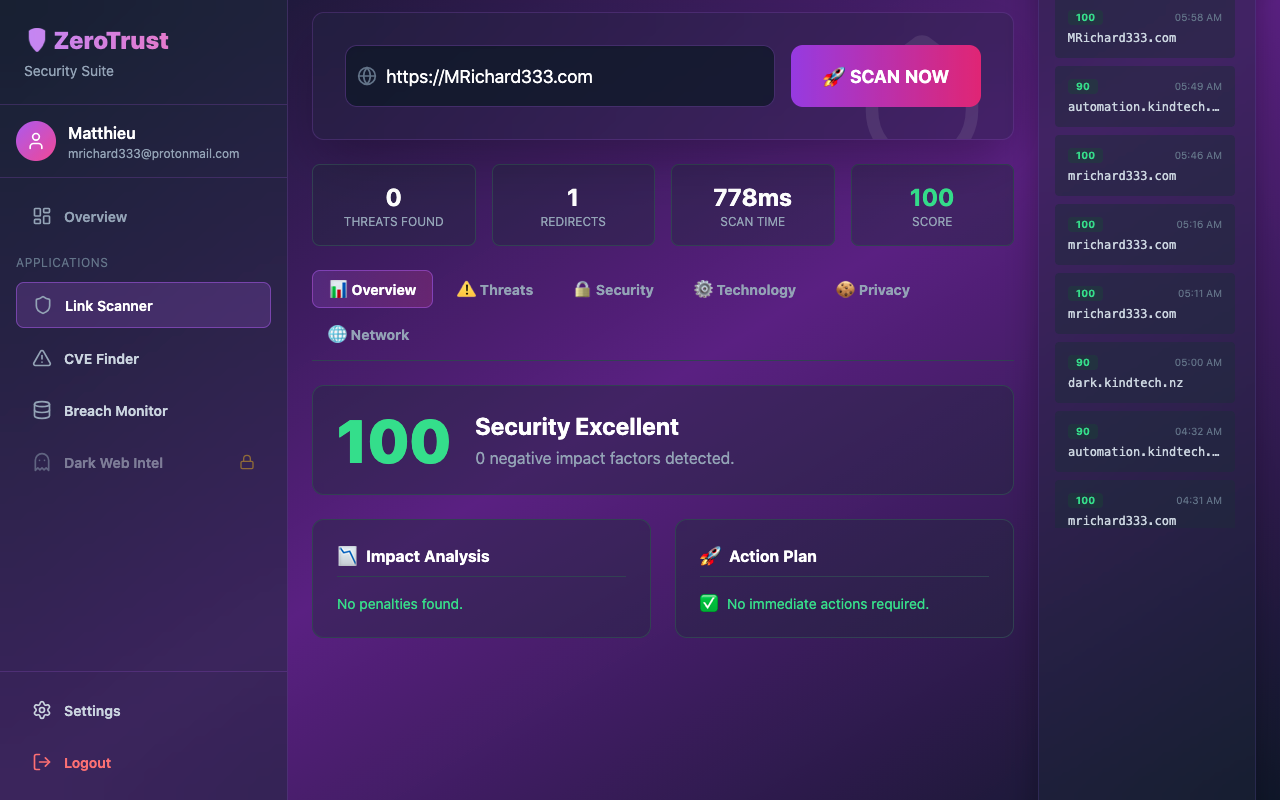
The score (0-100) is a weighted algorithm. We penalize for Missing SSL (-30), Phishing Keywords (-40), and Blacklisted IPs (-20). Conversely, we boost the score for valid security headers (like HSTS or CSP) and long-established domain ages.
Hackers often use "link shorteners" or multiple redirects to hide the final destination of a virus. Our scanner follows every hop in the chain. If a link starts at tinyurl.com but ends at malware-site.ru, we reveal the Final Destination before you click.
The Privacy Tab analyzes the cookies the site attempts to set. We flag Insecure Cookies (which can be stolen over WiFi) and identify third-party Trackers (like advertising pixels) that monitor your behavior across the web.
Yes. We operate on an Anonymized Processing model. While we log connection IPs strictly for DDoS protection and legal compliance, these logs are never linked to the specific URLs you scan. We do not build user profiles based on your scan history.
Yes. The tool includes a JSON Export feature for developers who need raw data. You can also generate a live Security Badge (Embed Code) to display the trust score on your own website or share a direct link to the report.
Enjoyed this article?
Support the author — leave a quick review.
★ Make a ReviewRead our other articles